Convert email addresses into privacy-safe identifiers with Touchless PII Hasher
by Seth Shapiro, on November 17, 2020
Narrative’s Touchless PII Hasher lets you quickly and securely transform email addresses into privacy-compliant, sharable identifiers.
Email addresses have become the gold standard for how organizations share customer data. They’re ubiquitous, persistent, and promise to be around for a long time. But they’re also considered personally identifiable information (PII), which means they need to stay private and secure.
This seems to be a paradox for data-driven organizations, but it can be solved by email hashing.
Hashing email addresses—converting emails into indecipherable but deterministic hexadecimal strings—lets marketers and analysts identify customers across channels without compromising privacy. It’s an essential first step in monetizing or acquiring data.
But hashing email addresses isn’t easy. If you don’t know how to write code or process large datasets, your only option has been to find an engineer that does. (And engineers are expensive.)
Which is why we’re so excited to release the Touchless PII Hasher. Now anyone can hash a list of email addresses in seconds. All the processing takes place on your local computer, keeping your customers' personally identifiable information private and secure.
It’s fast, it’s free, and it protects your data—opening up a world of new insights and opportunities for your business.
Create privacy-compliant IDs from data you already have
Every business has valuable and sensitive data about their customers. And of course, businesses need to carefully protect this personally identifiable information in order to maintain trust, safeguard proprietary assets, and comply with international regulations. But there’s huge potential value in gathering data from diverse sources and using identifiers across activation channels.
Hashing email addresses lets you connect your data to a massive ecosystem of both historical and up-to-the-second information about consumer behavior, demographics, location, and more. Data from different sources can be securely cross-referenced (and easily monetized), yielding more value and insight than would ever be possible from isolated information.
Our Touchless PII Hasher allows any business—even those without “data” departments—to see beyond their limited perspective and learn more about consumer identity and behavior, without sacrificing privacy or security.
Marketers, business analysts, and researchers can now handle the hashing process themselves—in seconds—with more time to focus on data acquisition, onboarding, analysis, and activation.
Keep your data safe
Keeping your data safe means that it needs to be hashed by you, not by a third party. This ensures that sensitive data isn’t lost or stolen in transit, or shared with unreliable third parties.
With Touchless PII Hasher, you do the hashing yourself. No uploads, no inter-office transfers, no secret passwords. Your data never “touches” an external server or travels across the internet; the original data and the resulting file of hashed emails are accessible to you alone.
You can use the resulting list on the Narrative data collaboration platform or with any of your data partners.
Validate and hash massive lists with point-and-click ease
Our customers were constantly frustrated by email lists that were too big for Excel or Google Sheets to handle, or needed to be “cleaned” and pre-formatted prior to hashing. This made it hard for some organizations to take advantage of opportunities on the Data Streams Marketplace.
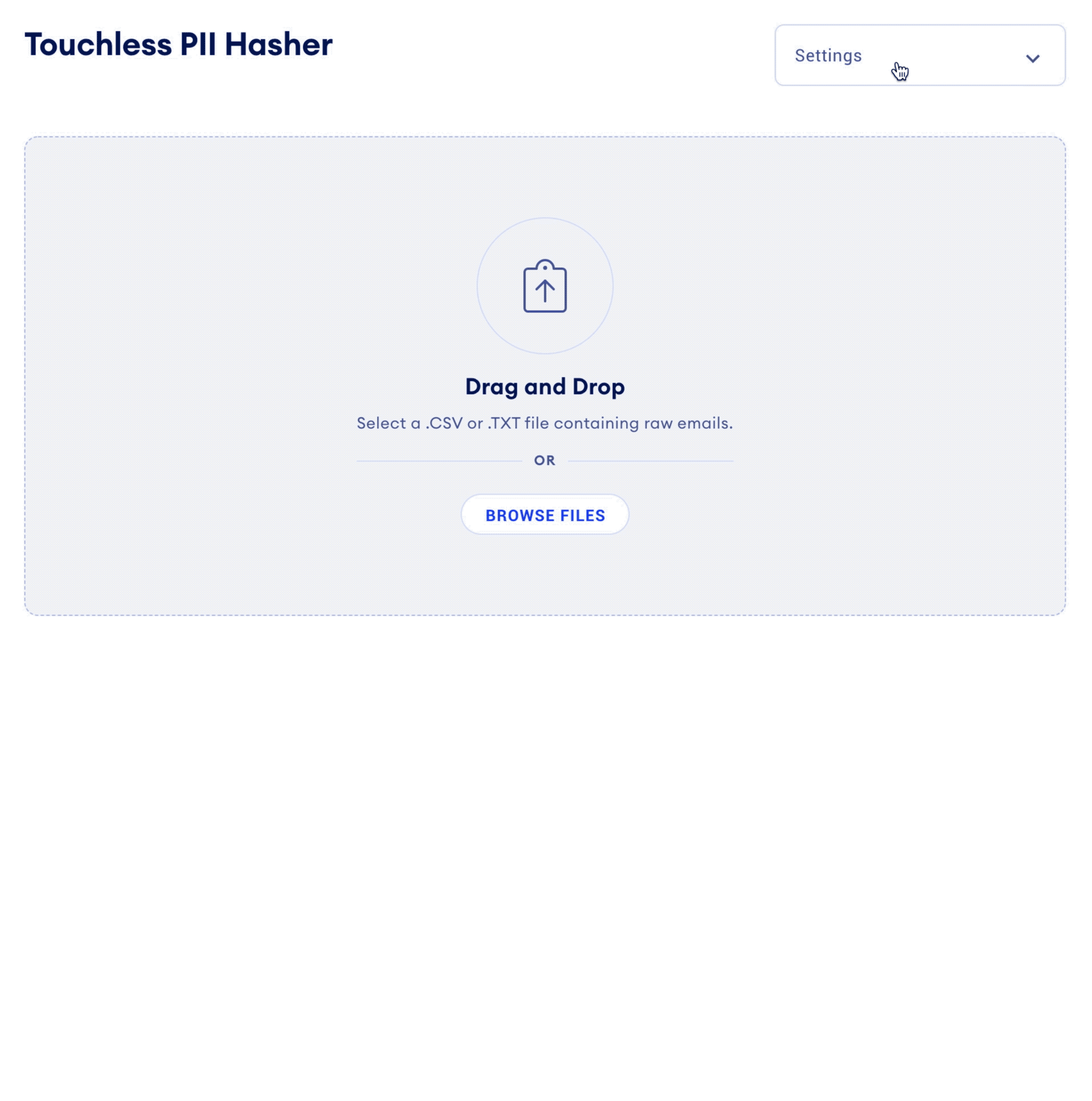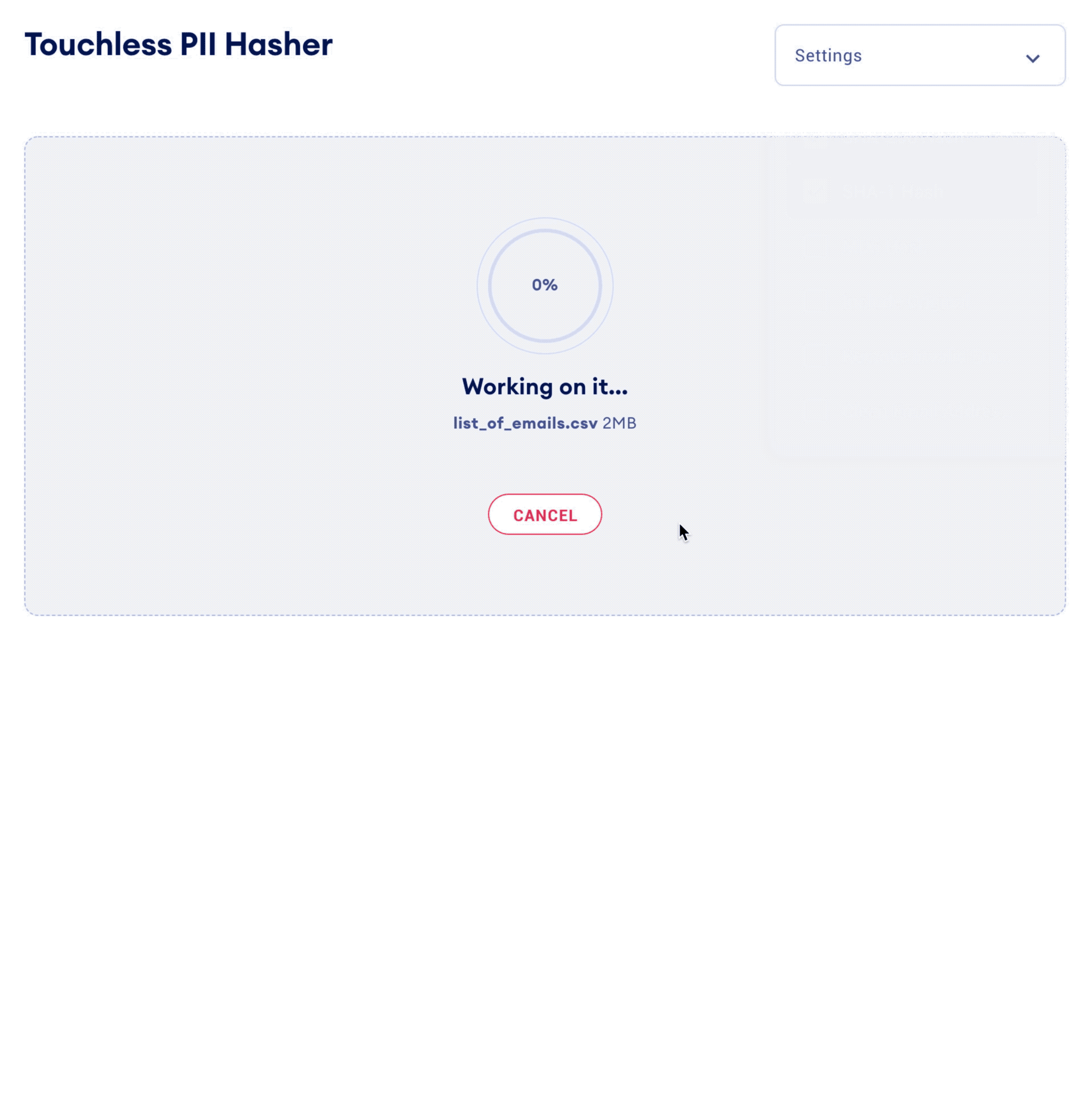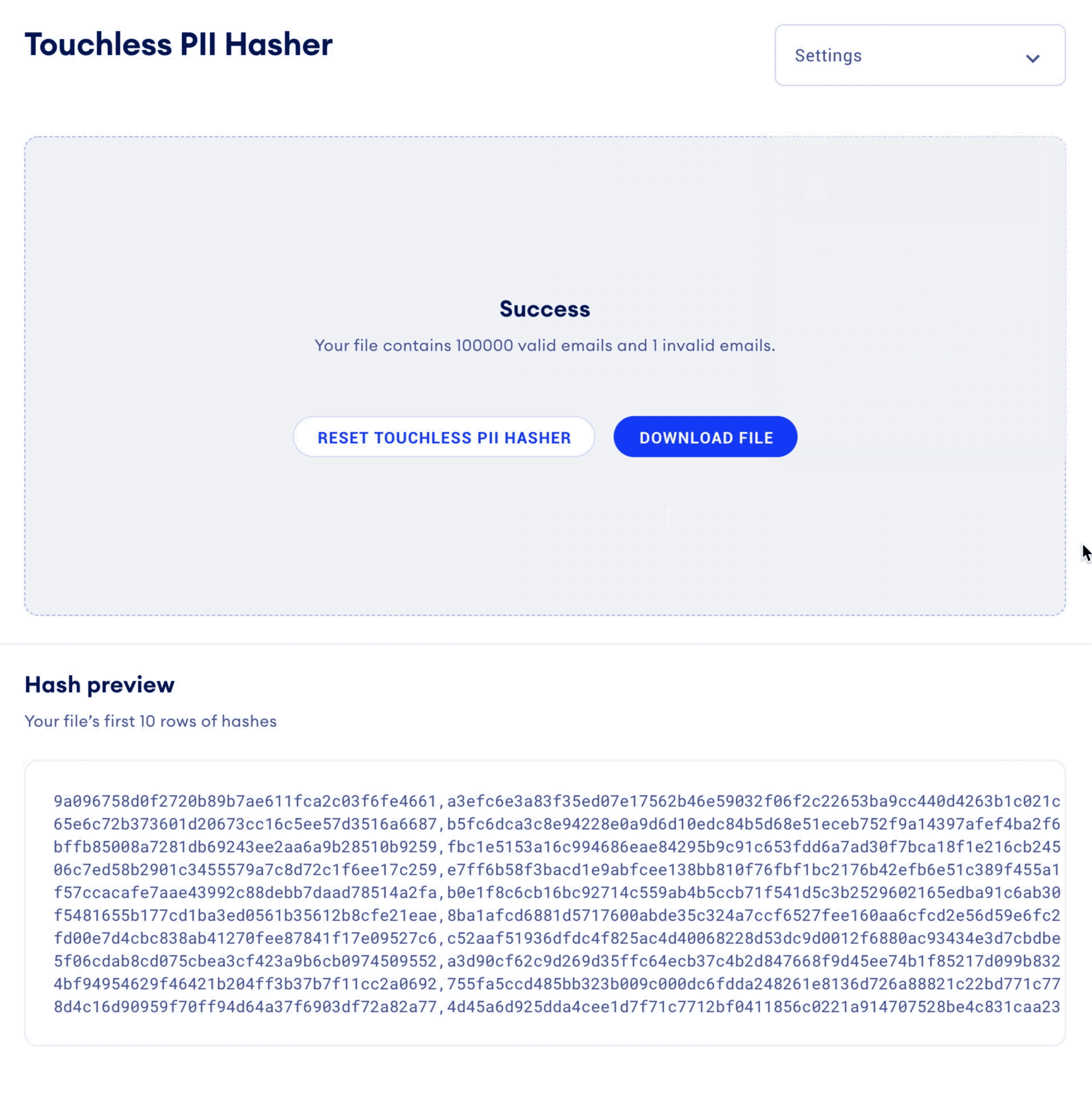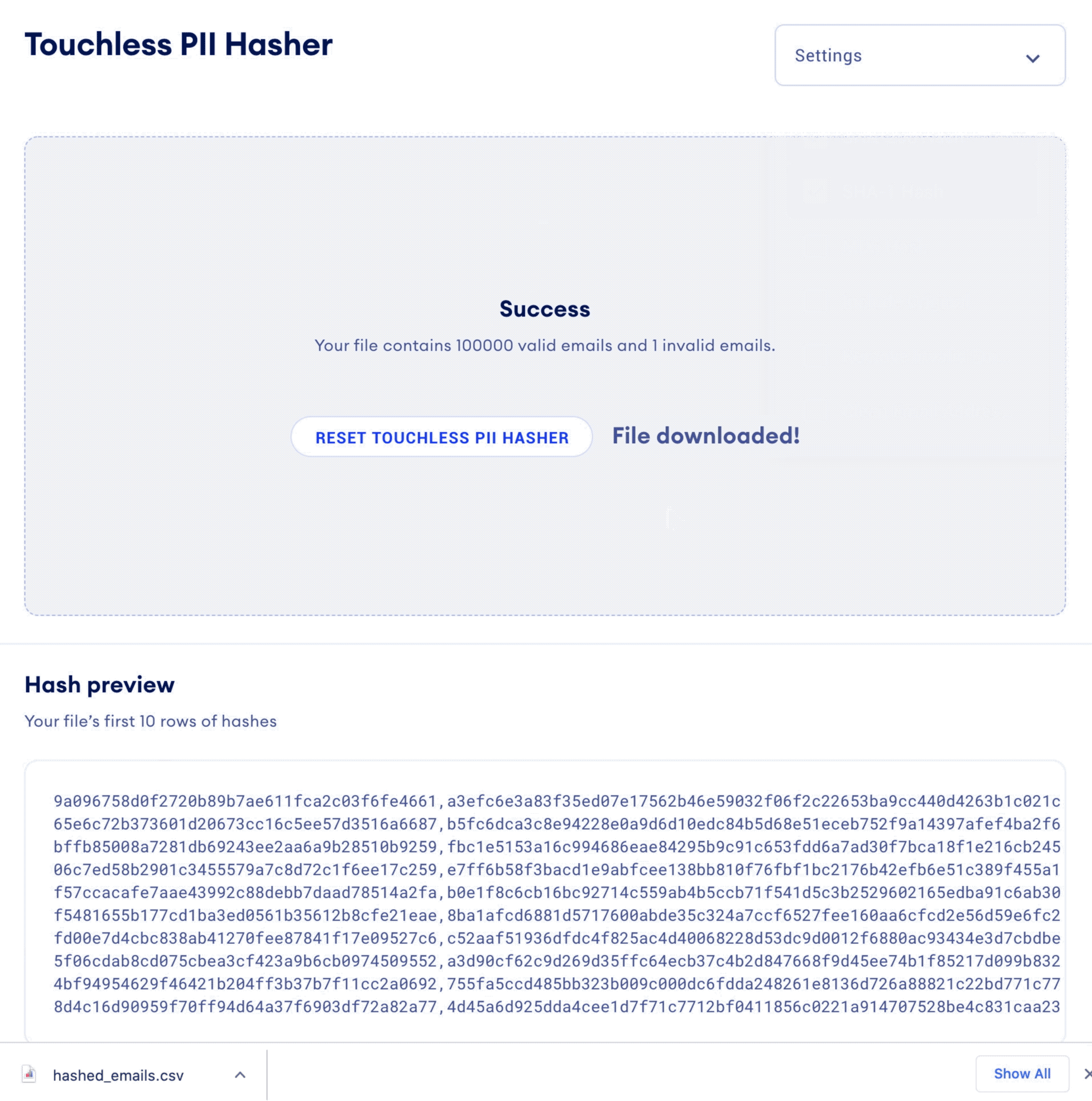
But now, buyers and sellers can use the Touchless PII Hasher to process millions of emails in seconds, no matter the size. It can also “clean” and pre-format your list of emails prior to hashing in accordance with industry standards, to ensure that your hashed emails will be compatible with other data in the ecosystem. With just a few clicks, a CSV file of hashed emails is created and ready to use immediately.
Here's how it works:
- Select which hashing function(s) you'd like to use to hash your emails: MD5, SHA-1, and/or SHA-256.
- Upload your list of emails as a CSV or TXT file.
- Click “Generate Hash.”
Get hashing!
Touchless PII Hasher is available for free to everyone.
If you’d like to learn more about how Touchless PII Hasher works, visit the knowledge base or schedule a call with a member of our sales team.